Not long ago, the Non-Fungible Token (NFT) and metaverse frenzy made the crypto industry appear to be all cheese and champagne. Then, in the first half of 2022, the digital assets market fell prey to a series of crypto rug pulls and hacks.
But what are rug pulls and hacks exactly? How different are they, and what can you do to stay safe?
Rugpulls vs. Hacks: The basic difference
As you know, transactions usually involve the producer and the consumer. When the producers themselves steal from the consumer, metaphorically pulling the rug from under their feet, it is a rug pull or scam. On the other hand, if a third party attempts to steal from both parties, it’s a hack, attack, or exploit.
Let’s take an example. One fine morning, if the bank makes a run with the customers’ funds, it will be marked as a scam—or a rug pull in crypto parlance. But in the case of a bank robbery, the robbers are the third party. They leave both the customer and the bank without money. That’s a hack.
What is a crypto rug pull?
With crypto rug pulls, developers cause the people who place their trust in their project to lose money. The developers of such projects are a lot like antiheroes—“good” guys who turn out to be bad eggs. However, rug pulls are of two types.
Hard Rugpulls: Most people are familiar with this kind of rug pull, and we focus on it in this article. They are well-planned; the community’s trust is secured primarily with the intention of stealing from them.
Soft Rugpulls: When tokens are devalued tokens because the developers are desperate and decide to dump their crypto assets overnight as a result of their desperation, it is called a soft rug pull. While such pumping-and-dumping is viewed as unethical, it may not be considered a criminal act.
According to a Chainalysis Report, scamming revenue rose 82% in 2021 to $7.8 billion worth of crypto. The firm noted that over $2.8 billion came from rug pulls.
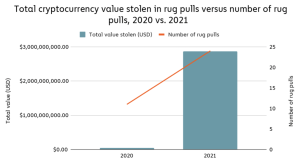
Two domains in crypto—NFTs and Decentralized Finance (DeFi)—have witnessed the rug pulls of recent times.
NFT rug pulls
Rupulls in the NFT space do, unfortunately, affect the “safest” projects—blue-chip projects. Blue-chip status is like a blue tick on Instagram or Twitter. People use it to check the trustworthiness of a project.
Investors usually believe that blue-chip projects are sustainable long-term investments. And that is precisely why rug-pulling developers take advantage of those who invest in them. Properties of such projects are first cloned. Then, after a while, the founders abandon the project, making away with members’ funds.
In November 2021, for instance, the users of a project inspired by the Squid Game TV show fell prey to one such scam.
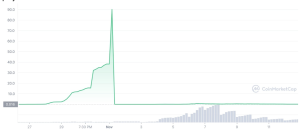
The chart above captures the native token SQUID’s sudden and phenomenal surge by close to 2,400% in a 24-hour window and subsequently drop to zero after the developers disappeared with member funds. A wave of NFT rug pulls followed soon after.
DeFi rug pulls
With rug pulls in the DeFi space, the developers of a project drain funds from the liquidity pool and disappear, sending the token’s value to zero.
A recent DeFi scam involved Blur Finance, a yield aggregator operating on BNB Chain and Polygon. However, the project developers suddenly abandoned it earlier this year, deleting its social media channels. According to security firm PeckShield, tokens worth over $600,000 vanished in the process.
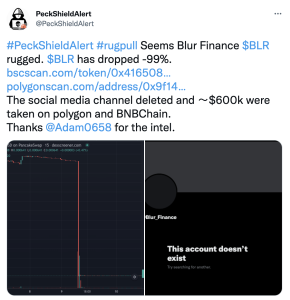
Source: Twitter
What are crypto hacks?
Crypto hacks occur when external entities steal from crypto platforms, businesses, or individual retail investors. A hacker can steal crypto in a much larger variety of ways, some of which we will discuss below.
Cyberattacks
In cyberattacks, hackers use malware, phishing, ransomware, denial of service, and other external virus-based attacks to disable a crypto platform’s systems and steal data. They may also use the breached platform as a launch point for other attacks.
One of the most prominent examples involves North Korea. At the start of 2022, news of North Korea launching cyberattacks on crypto exchanges broke. Some reports suggest the stolen crypto funds the nation’s nuclear and ballistic missile programs.
DeFi hacks
Along with cyberattacks, DeFi hacks also caught the spotlight. Defi protocols account for nearly 97% of all crypto stolen in the first three months of 2022, according to the aforementioned report from Chainalysis.
DeFi attacks are of two kinds: flash loan attacks and code exploits. The chart below, which draws on the Chainanalysis data, should give you a fair idea about the prevalence of each of these attacks.
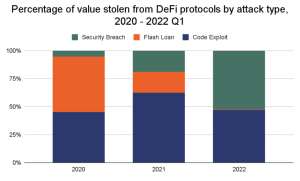
Now, let’s see what each of these types means.
1. Code exploits
If a hacker finds a bug, a.k.a. a software vulnerability or flaw in the security systems of a DeFi protocol, they could exploit that knowledge to steal from users and the protocol. This type of attack is a code exploit.
A recent example is the one on the cross-chain token bridge Nomad, which drained the network of nearly $200 million.
Cross-chain bridges help users send and receive tokens across blockchains. They lock tokens in a smart contract on one chain and then send them to the other in this “wrapped” form.
In Nomad’s case, the smart contract depositing their tokens was compromised due to an update, rendering the wrapped tokens worthless. A new report from Coinbase shows that 88% of the hackers, in this case, copied the key attacker’s code to execute their attack.
2. Flash loan attacks
A flash loan attack happens when hackers exploit flash loans. These attacks are much more complicated than code exploits. They require extensive planning to pull off successfully.
Let’s look at an example that will help you understand how extensive these scams can be. Earlier this year, a bunch of attackers managed to collect an airdrop meant for owners of two premium NFT projects, BAYC and MAYC. How did they manage to pull this off?
First, the attackers bought themselves an Ape NFT via the NFT marketplace, OpenSea. Then, they used this purchase as collateral to initiate a flash loan. The loan enabled them to access five BAYC NFTs secured in a vault. The hackers then claimed the airdropped APE token with the five borrowed BAYC NFTs.
The airdrop developers had not anticipated that NFTs borrowed through a flash loan could be used this way. They had not ensured that those claiming this kind of temporary “ownership” could be weeded out. The hackers had managed to identify and exploit this loophole.
How can you protect yourself?
Security-related threats are inevitable in most industries, but ours is seen as particularly vulnerable. Not falling prey to FOMO (the fear of missing out) helps, but DYOR helps even more.
You should always do the following:
- Verify the credibility of project developers. Ask: “Do the founders have substantial proof of work in the crypto industry? What is their track record?
- Check the Total Value Locked (TVL) in the project. TVL is a measure only specific to DeFi projects. It shows how successfully the project has attracted active and monthly transacting users. It is an especially important metric for lending and staking platforms, as a low TVL can directly affect the end user.
- Look for sudden or massive price hikes in new DeFi coins. If in doubt, use a block explorer—a web application that provides crypto transaction-related data, including addresses and fees, about blockchains—to make decisions.
To sum it up, “Don’t trust, verify.”
FAQs
Can a crypto recover from a rug pull?
while recovery from a rug pull is challenging, it is not impossible. Community support, legal actions, transparency, and improved security measures can all play a role in the potential recovery of a cryptocurrency project after a rug pull. However, prevention and due diligence remain the best strategies to avoid such scams in the first place.
Are rug pulls illegal crypto?
while rug pulls are widely seen as unethical and fraudulent activities in the crypto space, their legality can be complex and may depend on various factors. Investors are advised to be cautious and informed to minimize the risk of falling victim to such scams.
What is the most famous crypto rug pull?
The most famous crypto rug pull in history is associated with the cryptocurrency known as OneCoin. OneCoin is infamous for being one of the largest and most elaborate cryptocurrency scams ever recorded. It was founded by Ruja Ignatova and operated from 2014 to 2017, amassing a staggering $4 billion from unsuspecting investors.
Can a crypto recover from a rug pull?
Recovery for investors in a cryptocurrency after a rug pull is challenging but not impossible. A rug pull typically occurs when the creators of a crypto project suddenly abandon it, taking a significant portion of the funds invested with them.