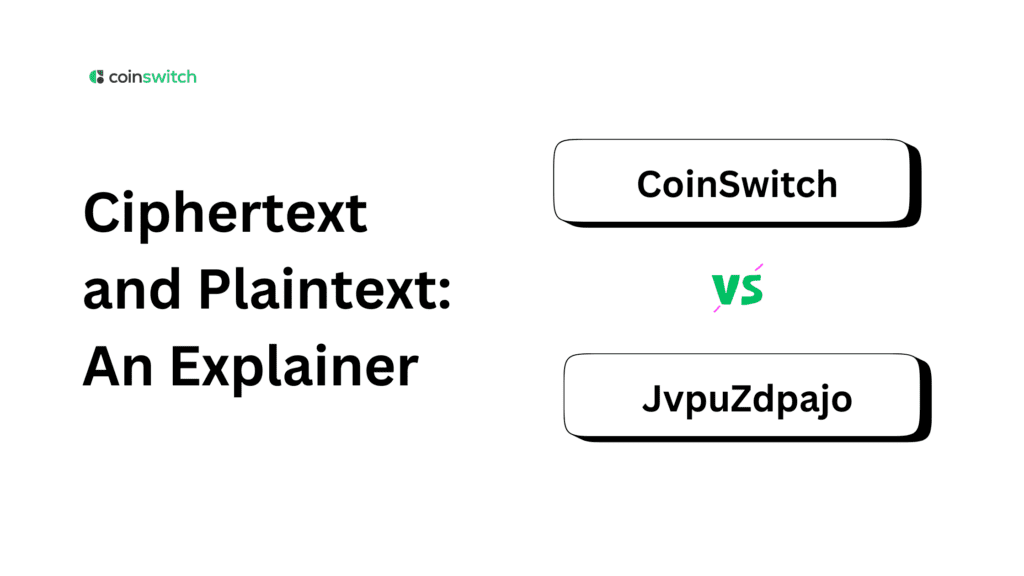
You type a message, hit send, and think it zooms across the internet intact. But it doesn’t. Before your message ever leaves your device, it’s scrambled. That scramble is the heart of security. The readable message is plaintext. The scrambled, unreadable version is ciphertext. Understanding what is ciphertext is key to understanding digital privacy. Ciphertext is a cryptographic approach where an algorithm utilizes substitutions instead of the original plaintext elements.
Without encryption, hackers would see everything: every password, every private chat, every bank detail, all in plain view. But by converting plaintext to ciphertext, we protect data during transit and storage. The encrypted version is useless to anyone without the proper key.
In this blog post, we’ll discuss:
- What exactly do plaintext and ciphertext mean
- Real examples
- Different kinds of ciphers
- How asymmetric and symmetric encryption differ
- Where ciphertext is used, emails, messaging, crypto
- And why this matters to you
Let’s dig in.
Understanding Ciphertext and Plaintext
Let me lay it out simply:
- Plaintext is your original message, the data in its readable form. What you type. What you save.
- Ciphertext is the result after encryption. It’s the same message, but scrambled beyond recognition.
Think of plaintext like a letter you write. Ciphertext is that letter locked in a vault. Only the right key opens the vault.
When someone intercepts ciphertext, they see gibberish. They don’t see your name, your password, or your credit card number. Without decryption, ciphertext is useless.
Encryption is the process: plaintext → ciphertext.
Decryption is the reverse: ciphertext → plaintext.
Modern ciphers ensure that even if someone knows the encryption algorithm, without the key, they cannot recover the plaintext. That’s the magic of cryptography.
Read More: What Is Fully Diluted Valuation (FDV) In Crypto?
Ciphertext Example
Let’s discuss a real example to make this less abstract.
Plaintext: “HELLO”
We apply a simple Caesar cipher shifting letters by 3.
- H → K
- E → H
- L → O
- L → O
- O → R
So ciphertext becomes “KHOOR”.
Here, HELLO is readable plaintext. KHOOR is ciphertext. The shift makes it unreadable unless someone knows to shift back by 3.
Now, scale this to modern systems. Imagine sending “Transfer ₹5000 to A1234”.
Modern encryption might turn that into:
4f:9A$G2#18N!x~kL
That jumble is ciphertext. Only the system with the right key can decrypt it and reveal the original instruction.
In everyday life, when you log into your bank, that process uses encryption so the password you type becomes ciphertext in transit. A hacker intercepting traffic sees only the scramble, not your actual password.
Read More: What is a Blockchain Consensus Mechanism?
Types of Ciphers
There’s no one way to encrypt. Cryptographers use different ciphers depending on need, speed, security, size, or computational cost.
Substitution Ciphers
Replace each unit (letter, number) with another according to a rule. The Caesar cipher is the classic example. Weak by today’s standards, but historically important.
Transposition Ciphers
Don’t replace characters; shuffle them. For example, “HELLO” → “LLEHO” by rearranging letters. Combine substitution + transposition for more complexity.
Block Ciphers
Modern encryption often works in blocks, fixed-size chunks of data. Each block passes through mathematical transformations using the key. AES (Advanced Encryption Standard) is a widely used block cipher. It’s fast, secure, and supports massive data encryption.
Stream Ciphers
Instead of blocks, encrypt bit by bit in a data stream. Useful when data arrives continuously, like live video or voice calls.
Hybrid & Modern Ciphers
Complex systems may combine block and stream techniques, use multiple rounds of transformation, or layer asymmetric + symmetric ciphers. The goal: make ciphertext uncrackable without massive computing power or the key.
For example, the one-time pad is theoretically unbreakable if done right: the key is as long as the message, absolutely random, and used only once. But distributing such keys securely is impractical for most systems.
Another is the Vigenère cipher, a polyalphabetic substitution where each letter’s shift depends on a repeating key. More complex than Caesar, but still breakable with frequency analysis.
Modern cryptography uses advanced, computationally secure algorithms. Classical ciphers are mostly used for learning.
Asymmetric-Key Ciphers
Asymmetric encryption is a game-changer. You use two keys: a public one and a private one.
- The public key encrypts plaintext into ciphertext. You share this openly.
- The private key decrypts that ciphertext back into plaintext. You keep it secret.
Here’s how it works in practice:
You want to send Jane a secret. Jane publishes her public key. You take your message (plaintext) and encrypt it with her public key. That becomes ciphertext. If Eve intercepts it, she sees nothing meaningful. Only Jane, holding the private key, can decrypt it and read the original message.
This system underpins SSL/TLS for secure websites, digital signatures, PGP emails, and blockchain wallets.
The beauty: no shared secret key needs to travel insecure channels. Even if someone sniffs your public key, they can’t derive the private key (with strong algorithms). The relationship between public and private is mathematical but one-way.
Symmetric-Key Ciphers
Symmetric encryption uses the same key to encrypt and decrypt. Both parties must share this secret key ahead of time.
Plaintext + key → encryption → ciphertext
Ciphertext + same key → decryption → plaintext
This method is fast and efficient, great for bulk encryption. But the key distribution is the tricky part: how do you safely share the key? If a third party intercepts the key, they can decrypt every message.
AES is the dominant symmetric cipher. It encrypts data blocks using rounds of substitutions, permutations, and mixing, governed by the key. It’s efficient, secure, and widely used.
In many systems, data is first encrypted using symmetric encryption and then the symmetric key itself is encrypted using asymmetric encryption (public-key). That gives both speed and security.
Uses of Ciphertext
Every time you sense “digital security,” ciphertext is working behind the scenes.
- Messaging & Chats: WhatsApp, Signal, iMessage encrypt your messages into ciphertext before sending. Only recipients decrypt them.
- Banking & Finance: Passwords, transactions, and account details in plaintext are converted into ciphertext so that even if communication is intercepted, the data is unreadable.
- Cloud Storage: Files stored in cloud servers are often encrypted. The storage provider may hold ciphertext; only the user with the key can decrypt.
- VPNs & Secure Channels: Your internet traffic becomes ciphertext over the tunnel, hiding your browsing from eavesdroppers.
- Blockchains & Crypto: Private keys, transaction data, and wallet addresses all rely heavily on encryption to transform plaintext into ciphertext.
Without ciphertext, every digital secret would be exposed.
Email Ciphertext
Email is old, reliable, but risky if unprotected. Historically, emails traveled as plaintext. Anyone intercepting them could see everything.
Today, most email systems use transport-level encryption (TLS) to convert messages into ciphertext while moving between servers. But that doesn’t encrypt messages end-to-end. On the server, emails may revert to plaintext unless you use encryption tools like PGP or S/MIME.
PGP (Pretty Good Privacy) encrypts your message itself. You encrypt plaintext into ciphertext before sending. Only the intended recipient, with a private key, can decrypt it. Anyone else intercepting sees only ciphertext.
For example, sending your tax document without encryption sends plaintext. A hacker intercepts it. Game over. Encrypt it into ciphertext. They intercept. They see gibberish. Keyholders decrypt. Only they see the data.
This extra layer matters when secrecy is important.
Conclusion
Understanding what is ciphertext and plaintext are isn’t just technical jargon; it’s central to your privacy and security online.
Plaintext is your message in clear form. Ciphertext is that message scrambled, unreadable to all but authorized eyes. Encryption and decryption transform between the two.
From Caesar’s simple shift ciphers to today’s AES and RSA systems, the goal remains the same: keep secrets secret. Every chat, transaction, and connection depends on a ciphertext protecting its content.
Next time you send sensitive info, passwords, account numbers, or messages, know that ciphertext is doing the heavy lifting, turning vulnerabilities into protected communication.
FAQs
1. What is plaintext and ciphertext?
Plaintext is information in its original, readable form. It’s what you type in a message, save in a document, or say in a chat. Anyone can understand plaintext without needing a key.
Ciphertext is the encrypted version of that same message. It looks like gibberish to anyone without the key to decrypt it. Encryption turns plaintext into ciphertext. Decryption flips it back.
For example:
Plaintext: “Send ₹10,000 to Raj.”
Ciphertext (AES-encrypted): “o3#Z1lx$983Pq@!7”
This transformation protects sensitive data while it travels or sits in storage.
2. What is plain text?
Plain text is any data in a readable, unencrypted format. It could be a sentence, a password, a number, or a full document, anything written in natural language or standard coding syntax.
Think of plain text as something anyone can open and read with no special tools. Whether it’s “Hello World” in an email or your ATM PIN in a backend system, if it’s not encrypted, it’s plain text.
Developers often use plain text for code, JSON, logs, or basic documents. Security systems use it as the starting point before encryption kicks in.
3. What is ciphertext with an example?
Ciphertext is what you get when you scramble a message using encryption. It hides the meaning, even if someone sees the data.
Example:
Plaintext: “Meeting at 5 PM.”
Encryption method: Caesar cipher (shift letters by 3)
Ciphertext: “Phhwlqj dw 5 SP.”
Modern encryption turns messages into even more complex strings, like:
“6Ajh!$#Zk_19@Xqo3”
Without the correct decryption key, that jumble reveals nothing. It’s how banks protect passwords, how messaging apps secure chats, and how data stays private on the web.
What is ciphertext in blockchain?
In blockchain systems, ciphertext protects wallet data, smart contract interactions, and off-chain messages. It ensures that sensitive data, like private keys or encrypted messages, stays unreadable to the network or outside observers.
For example:
When someone signs a transaction, their private key doesn’t travel in plaintext. Instead, it’s used to generate an encrypted digital signature (a form of ciphertext). The network can verify that it’s valid, without ever seeing the private key itself.
Some blockchains also support fully encrypted messages, like zk-SNARKs on Zcash or homomorphic encryption tools in privacy-focused protocols.